A Comprehensive Security Checklist for Your Sitecore-Based Website
In today's digital world, web security is a non-negotiable priority. Whether you're a Sitecore website developer, user, or client, understanding the critical aspects of web security is essential. To help you ensure the robust security of your Sitecore-based website, we've created an extensive security checklist based on globally accepted standards, including the OWASP Top 10, SANS, WASC, CWE, and more. Our goal is to provide you with a solid starting point for securing your Sitecore site while promoting best practices within the industry.
OWASP Top 10 Application Security Risks 2023
Our checklist is built around addressing the critical security vulnerabilities outlined in the OWASP Top 10 Application Security Risks 2021.
- - A01:2021-Broken Access Control
- - A02:2021-Cryptographic Failures
- - A03:2021-Injection
- - A04:2021-Insecure Design
- - A05:2021-Security Misconfiguration
- - A06:2021-Vulnerable and Outdated Components
- - A07:2021-Identification and Authentication Failures
- - A08:2021-Software and Data Integrity Failures
- - A09:2021-Security Logging and Monitoring Failures
- - A10:2021-Server-Side Request Forgery
Specific Security Concerns for Sitecore Websites
Remote Code Execution via Unrestricted File Upload (A04:2021-Insecure Design)
In Sitecore XP/XM 10.3, a vulnerability (CVE-2023-26262) was identified that allows authenticated Sitecore users with administrator rights to upload files with malicious intent. This can result in code execution on the content management server. Exploiting this flaw allows an attacker to compromise the integrity and confidentiality of the application and potentially gain unauthorized access to sensitive data.
Recommendations: To address this critical vulnerability, it is essential to implement robust security measures that can prevent unauthorized file uploads and protect the system from malicious code execution.
Disable the dialog for specific users by denying them "Read" access right to the
‘/sitecore/content/Applications/Files/FileBrowser‘ and
‘/sitecore/content/Applications/Files/FileExplorer‘ item in the Core database.
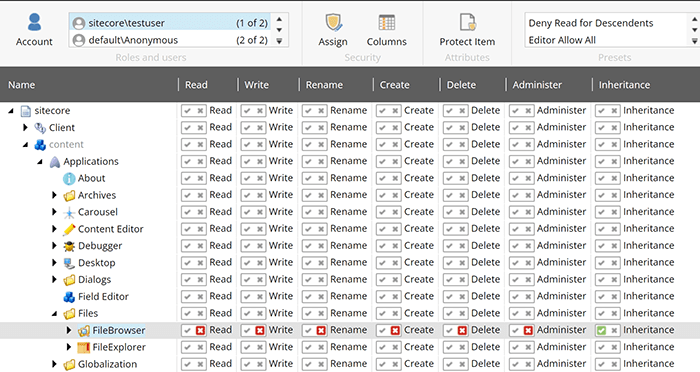
Deny Script and Execute permissions for the temp and upload folder: As a website administrator, you can turn down the requests to run scripts and executable files in the upload folder. As a result, this will help you prevent an uploaded file to be executed on the server side when a user tries to download it. All details are mentioned in Sitecore’s official documentation.
To mitigate this risk, implement file type restrictions for uploads and enforce deny script and execute permissions for the upload folder in Sitecore.
Missing Antivirus Protection on Sitecore Media Upload (A04:2021-Insecure Design)
The Media Library upload function can allow users to upload malicious files or scripts without restrictions. This increases the attack surface, potentially leading to the execution of malicious code. To reproduce the issue, we tried to upload an EICAR file to the Sitecore media library and observed that it downloadable and accessible from the CM and CD server.
Recommendations: It is recommended to implement antivirus protection for the media library's upload function. While Sitecore doesn't provide this out of the box, you can customize a solution. Additionally, limit the types of files that can be uploaded and verify their content, ensuring that they adhere to expected standards.
Insufficient Session Expiration (A07:2021-Identification and Authentication Failures)
Inadequate session timeout settings can lead to session hijacking attacks, particularly in public computer scenarios. If a user forgets to log out on a public computer, an attacker could easily access their account by pressing the back button. By default, Sitecore sets the session time-out value to 60 minutes (1 hour). This means that if a user remains inactive for 60 minutes, their session will expire, and they will be automatically logged out of the system. However, there are scenarios where you may need to modify this default behaviour and customize the session time-out based on specific requirements.
Recommendations: To handle sessions properly, ensure that the application code creates, maintains, and destroys session tokens over a user's session lifecycle. Consider configuring session timeouts in Sitecore, there are three key settings that need to be modified in the Sitecore.config and identity server. These settings control different aspects of session management in Sitecore. Change the value of Authentication.ClientSessionTimeout in Sitecore.config.
Improper Error Handling (A05:2021-Security Misconfiguration)
Incorrect error handling can expose sensitive information about your application's infrastructure. Some application displays stack traces in error messages with technical details. This information can assist an attacker as it provides valuable information about the platform and configuration which may be used to further target the attack. This information can be used by an adversary to launch further attacks on the application.
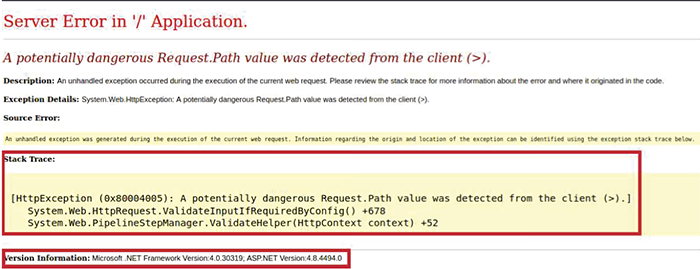
Recommendations: Avoid displaying technical details, stack traces, or revealing platform and configuration information in error messages. All errors should be managed by the application, and generic error messages should be displayed. In Sitecore, you can configure custom error pages for different HTTP error codes like 404 or 500.
Also, you can configure removeServerHeader via web.config.
<system.webserver>
<security>
<requestfiltering removeserverheader="true">
<security>
</system.webserver>
Secure Headers (A05:2021-Security Misconfiguration)
Ensure your Sitecore website's security headers are correctly configured. Leaving default configurations unchanged can introduce security risks. To enhance your website's security, implement key security headers in web.config.
Recommendations:
- X-XSS-Protection: Enabling the XSS Protection HTTP Response Header in the web application will prevent attackers from carrying out common reflected cross-site scripting attacks. X-XSS-Protection should be configured with “1; mode=block”
- Content-Security-Policy (CSP): CSP is a critical security header. However, the example CSP policy provided in Sitecore’s default configuration might need adjustments. It’s crucial to create a strong policy tailored to your website’s specific needs. C CSP is an added layer of security allowing you to detect and mitigate certain attacks, such as cross-site scripting (XSS) and data injection attacks. To enable CSP, you need to configure your web server to return the Content-Security-Policy HTTP header.
- X-Content-Type-Options: The X-Content-Type-Options HTTP header prevents content sniffing, ensuring that MIME types specified in the content types headers are not changed by the server. This helps block content-type sniffing attacks. Use X-Content-Type-Options: nosniff.
- HTTP Strict Transport Security (HSTS): The HTTP Strict-Transport-Security response header (often abbreviated as HSTS) informs browsers that the site should only be accessed using HTTPS, and that any future attempts to access it using HTTP should automatically be converted to HTTPS.
Cross-Origin Resource Sharing (CORS) Policy (A05:2021-Security Misconfiguration)
We have noticed sometime, the application implements an HTML5 cross-origin resource sharing (CORS) policy for the request that allows access from any domain.
Trusting arbitrary origins effectively disables the same-origin policy, allowing two-way interaction by third-party web sites. Configure your CORS policy correctly, allowing access only from trusted domains.
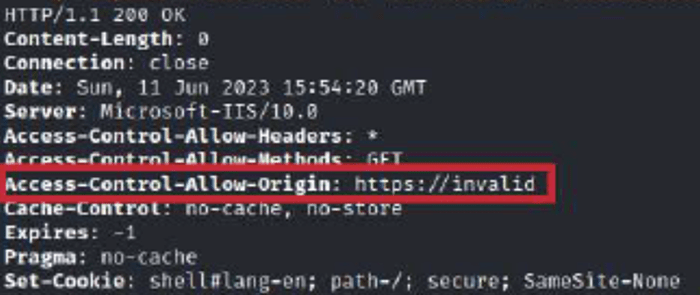
Recommendations:
For an SXA bases website, you can configure the CORS setting at site grouping.
/sitecore/content///Settings/Site Grouping//CORS 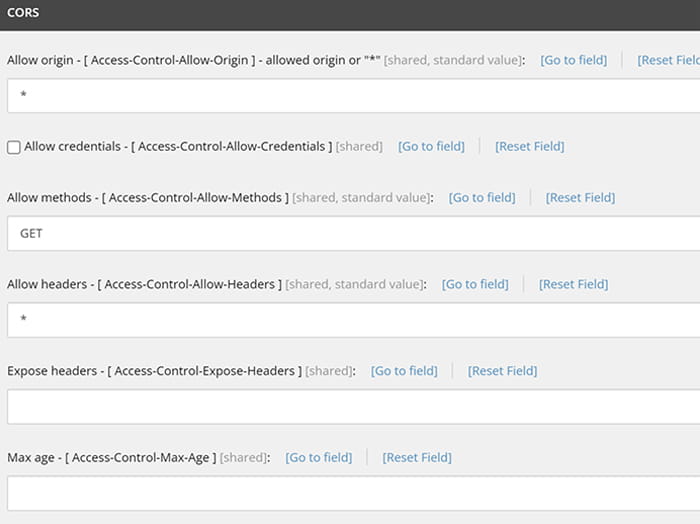
Conclusion
Web security is an ongoing endeavour. By adhering to this comprehensive checklist, you can reduce security risks, protect user data, and maintain the trust of your website's audience. Keep in mind that proactive security measures are essential in an ever-evolving threat landscape. Your Sitecore-based website's security is a critical investment that will pay off in safeguarding your digital assets and reputation.

